中山大学2024 CTF校赛 # writeup
零基础,可能某些描述比较奇怪
Sign In
根据题面在排行榜中找到W4terDr0p战队,flag在个性签名处 找到flag
broken.mp4
根据第一个视频,在微信中搜索找到这篇文章,找到视频修复软件,根据文章指示修复另一个损坏的视频。修复之后发现flag在视频中。
Remember It 0
利用手机录像记住十次字符串,得到flag
Shuffle Puts
用记事本打开即可找到flag
Revenge of Vigenere
首先遍历密钥长度从[10-20),根据密钥给密文分组,对每组遍历26个字母,假设该字母是密钥的基础上推出明文,计算出该组与自然英文的重合指数,选择重合指数最大的一个字母作为密钥。
代码如下
1 | import string |
运行之后,发现密钥长度12时出现flag

Spam 2024
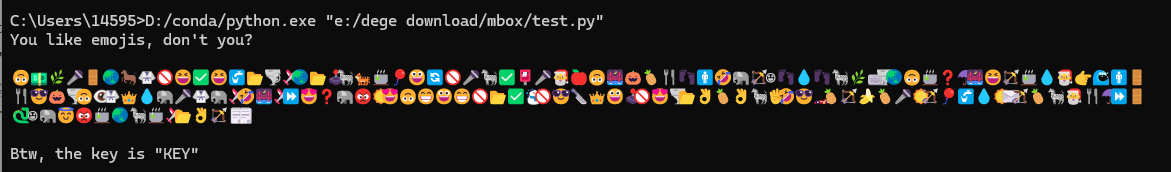
在spammimic - hide a message in spam中解码该垃圾邮件,得到一串十六进制,用python解码一下
1 | emoji_hex_string = "59,6f,75,20,6c,69,6b,65,20,65,6d,6f,6a,69,73,2c,20,64,6f,6e,27,74,20,79,6f,75,3f,0a,0a,01f643,01f4b5,01f33f,01f3a4,01f6aa,01f30f,01f40e,01f94b,01f6ab,01f606,2705,01f606,01f6b0,01f4c2,01f32a,263a,01f6e9,01f30f,01f4c2,01f579,01f993,01f405,01f375,01f388,01f600,01f504,01f6ab,01f3a4,01f993,2705,01f4ee,01f3a4,01f385,01f34e,01f643,01f309,01f383,01f34d,01f374,01f463,01f6b9,01f923,01f418,01f3f9,263a,01f463,01f4a7,01f463,01f993,01f33f,2328,01f32a,01f30f,01f643,01f375,2753,2602,01f309,01f606,01f3f9,01f375,01f4a7,01f385,01f449,01f30a,01f6b9,01f6aa,01f374,01f60e,01f383,01f32a,01f643,01f441,01f94b,01f451,01f4a7,01f418,01f3a4,01f94b,01f418,01f6e9,01f923,01f309,01f6e9,23e9,01f60d,2753,01f418,01f621,2600,01f60d,01f643,01f601,01f600,01f601,01f6ab,01f4c2,2705,2603,01f6ab,01f60e,01f52a,01f451,01f600,01f579,01f6ab,01f60d,01f32a,01f4c2,01f44c,01f34d,01f44c,01f993,01f590,01f923,01f60e,01f3ce,01f34d,01f3f9,01f34c,01f34d,01f3a4,2600,01f3f9,01f388,01f6b0,01f4a7,2600,2709,01f3f9,01f34d,01f993,01f385,01f374,2602,23e9,01f6aa,01f40d,263a,01f418,01f607,01f621,01f375,01f30f,01f993,01f375,01f6e9,01f4c2,01f44c,01f3f9,01f5d2,01f5d2,0a,0a,42,74,77,2c,20,74,68,65,20,6b,65,79,20,69,73,20,22,4b,45,59,22" |
得到如下图所示的结果:
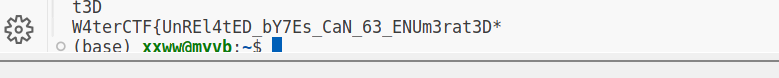
将这一串emoji放到emoji-aes (aghorler.github.io)中解码,猜测密钥为”KEY“,不正确。猜测密钥为🔑,解码结果如下为:0x???? ⊕ dxBUQVJndGJbbGByE3tGUW57VxV0bH9db3FSe2YFUndUexVUYWl/QW1FAW1/bW57EhQSEF0=。
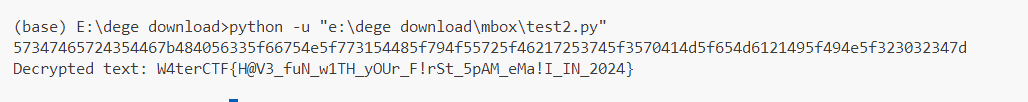
由等号猜测后面部分为base64编码,解码之后由⊕猜测需要与一个十六进制数进行异或。忙猜0x2024,得到flag。
代码如下:
1 | import base64 |
结果:
Wish
分析源码,可以知道需要适当的index和time提高概率,于是在本地测试:
1 | import requests |
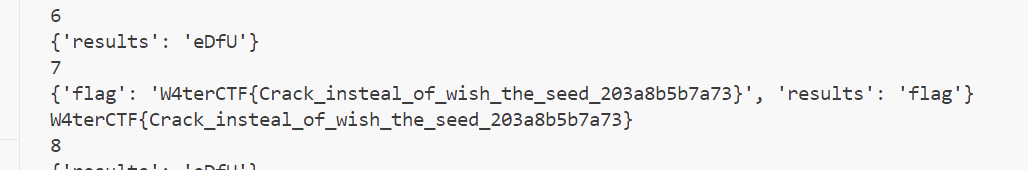
发现time为10693,index为2的时候,概率最大,然后写脚本抽flag。
1 | import requests |
顺利拿到flag
Smoke hints
1 | 114514 * x**2 - 11680542514 * y**2 + 1919810== 2034324 |
左右两边同时除以114514,可以整除,除后是一个佩尔方程,利用在线网站解一下得到x,y。
根据n = pq,和hint5解出p和q。得到phi_n。
1 | hint2 = (reduce(lambda x, y: x * y,range(1 ,hint1 - 1)) * e) % hint1 |
hint1是质数,所以(hint1-1)!=1 mod hint1,也就是e = hint2 mod hint1 。循环遍历一下e,根据phi_n和e得到d,再利用hint4检验e的正确性,得到e。最后利用pow(c,d,n)完成解密,得到flag。
代码如下:
1 | import gmpy2 |
User Manager
不断创建新用户包含secret的新用户,利用二分法找出flag
代码如下:
1 | import requests |
BruteforceMe
丢到IDA反汇编
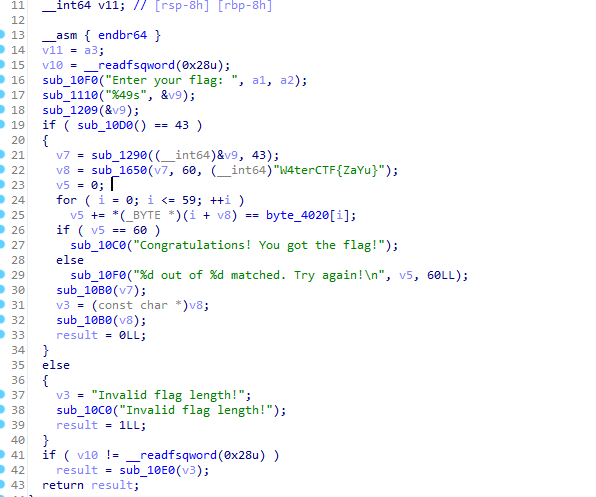
观察一下main函数,发现是把输入的字符串由43个字节转换为60个,之后在sub_1650中再经过一些变换,看一下sub_1290函数
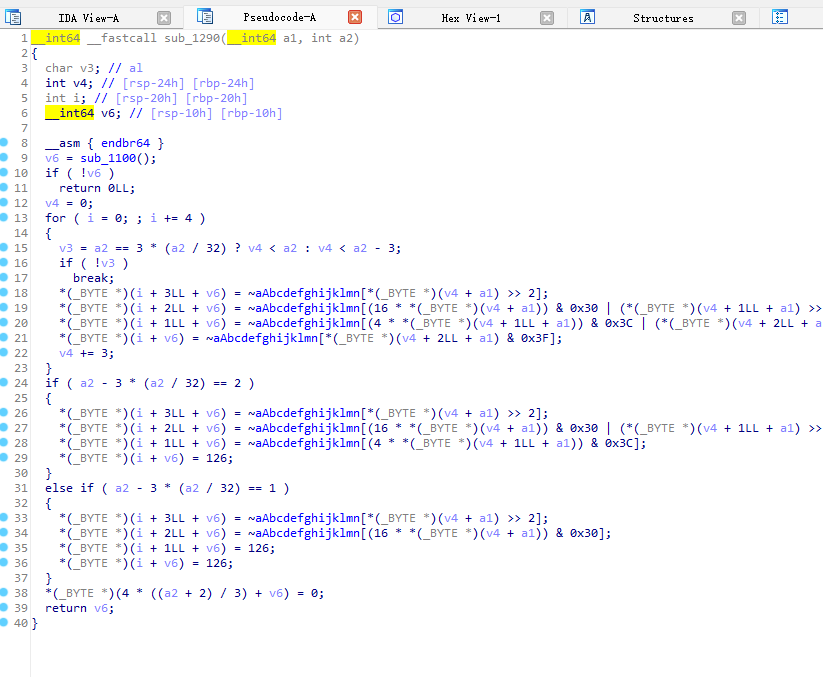
发现就是把每三个字节换成了四个字节。于是按三个字节一组暴力循环,通过输出的数字进行判断。
代码如下:
1 | import subprocess |